Since I am not able to predict the future and I don't have enough big picture expertise in InfoSec to make intelligent and plausible predictions, I am going to take the easy way out. I know it isn't exactly exciting and you might even call it lame, but I predict 2011 will bring more of the same. (I am not a poet, and I know it.)
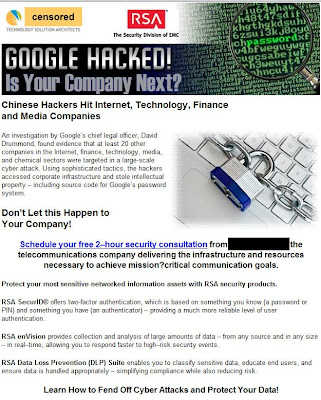
- Increasingly frequent financial data breaches ala TJX and Heartland
- Malware, malware, and STILL MORE malware - and likely even more crafty varieties
- Finally, the one that freaks me out most of all - more SCADA/Control System activity ala Stuxnet. Even without (alleged ;) government involvement, no doubt the bad guys took careful notes of the possibilities. The terrorists and government sponsored groups are likely pulling down additional copies of Siemens, Schneider, Rockwell, Modicon et al softwarez and likely also buying a representative bunch of PLCs to increase their mad skillz in pawning pumps, valves and variable frequency drives.